Walter Sprenger,
Compass Security When do we notice that we were a victim of a cyber-attack?
Mr Sprenger, when someone like you works in a company specialising in cyber security, which view do you take on digitalisation?
As a company and as specialists, we take an optimistic view of digitalisation. The more digital it all becomes and the more is transferred to the digital world, the more areas there are in which cyber security is required.
You are focussed on rendering companies secure and preparing them for cyber-attacks. What can be understood by the term “cyber-attack”?
I see primarily two basic forms of attacks on companies. On the one hand, there are those scenarios in which data is copied, i.e. stolen and in many cases, made public. On the other hand, there are attacks concentrating on hindering the operations of systems and infrastructures or paralysing them. The copying of data, as a rule, causes a more long-term and greater level of damage, whilst the paralysing of systems has, in comparison, a short-term impact.
«So long as the data is on-line in one form or another, it will be difficult to protect data from a well thought-through and targeted attack.
In both scenarios, we can in turn differentiate between general and targeted cyber-attacks. We can protect ourselves against general attacks by establishing a good basic protection. This is more difficult in the case of targeted attacks. Imagine a Trojan infiltrating the workplace of an employee. If the employee now has access to sensitive customer data, these can also be stolen by the Trojan. So long as the data is on-line in one form or another, it will be difficult to protect data from a well thought-through and targeted attack.
How does a targeted attack occur?
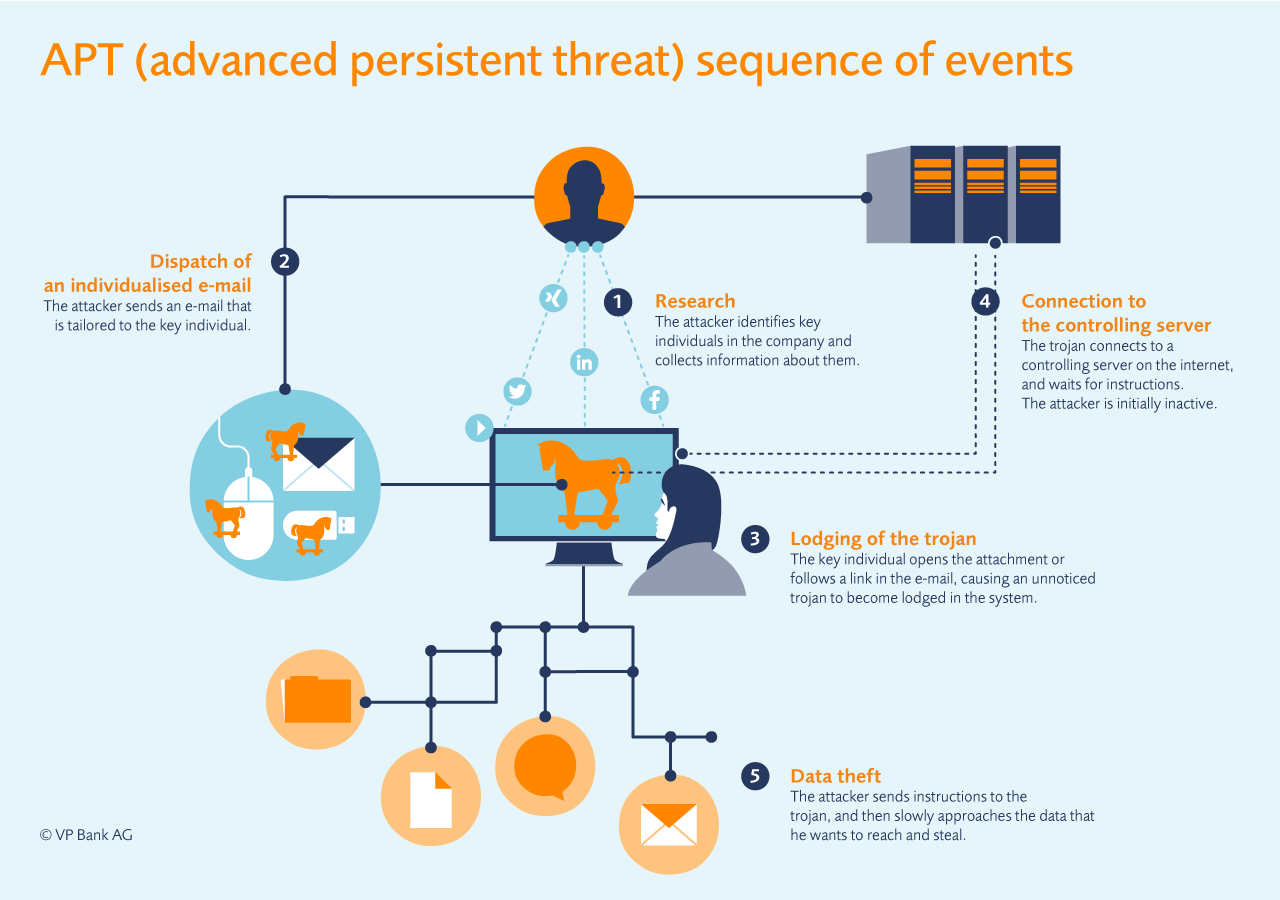
One speaks of APT, an advanced persistent threat. As a first step, the attacker or group of attackers inform themselves very well as to the company and identify individuals working in critical positions thus having access to a lot of information. As soon as the individuals are identified, the attackers attempt to find out as much as possible about the social environment of the selected employees. In the following step, the employees receive an e-mail which is tailored for them personally, ostensibly coming from a friend or acquaintance. As the text of the message is so specifically tailored to the individual, it provokes no suspicion on his part and he also possibly opens the information in the attachment to the e-mail. A Trojan lurks in the attachment which lodges itself in the system and at first does nothing except to establish contact, however, with a control server in the internet. Whenever the attacker someday wishes to come into possession of information, he will give the commands to the Trojan via the control server. He watches the rights the employee possesses and works slowly forward until he comes to the data which he actually wishes to steal.
You say that we all can become a victim of an attack without knowing it. Does this mean that attackers are smarter than us or that we do not have sufficient awareness of the dangers resulting from our digital actions?
I would say yes to both. Cyber-attackers are smart and their big advantage is that cyber-attacks can easily be multiplied. Only a few specialists are required to attack large masses. I can come up with an attack, write a programme and frequently perform attacks on numerous targets without needing further resources.
Furthermore, whether we act as companies or as private individuals, we must first get to know the new digital dangers. People generally learn if something has already gone wrong. They then begin to accept the danger, to define rules and to consciously manage their risk.
Do you find that improvements need to be made to existing laws?
Yes. I believe, however, that not only laws but also training is required. Because of the legal frontiers, laws for the digital world are mostly a difficult topic. There are nevertheless already new approaches for increased security: in Germany, for instance, operators of critical infrastructures are obligated to report incidents so that one can better evaluate the dangers. To regulate everything through laws, however, will hardly be possible, not least due to the speed of digitalisation which puts us in front of great challenges. Many areas are over-extended by the rapid pace.
And other areas adapt and speed up themselves…
I have the feeling that the ever-shorter time to market (TTM) has adverse effects. In spite of new products and technologies on the market, there are time and again the same weaknesses and security problems. Time pressure and possibly a lack of knowledge lead to new technologies not being developed in a secure manner right from the start.
We also notice repeatedly that human beings are the weakest link in the chain. There are those who develop products, and those who utilise the technologies. Human beings, however, are not perfect. As long as systems and products are not developed by machines themselves, there will always be mistakes and weaknesses.
«Anonymity will probably be a luxury commodity one day. It will be luxury that one’s own tracks will not be recorded.»
Can we, as customers and private individuals, say goodbye to the thought that our data is secure and we have control over who has access to our data?
Whenever it concerns, for instance, address data, customer data or personal data, then it is difficult to protect these as a private individual. It is interesting, however, to note that a change in approach to handling information is taking place. The young generation volunteers much data about themselves and regards the issue of security in a rather indiscriminate manner. Whenever I wish to protect extremely personal data, there are possible ways to do this. Whenever, however, I entrust someone with the data or someone collects data about myself, then I believe we ourselves no longer have control.
That is to say, you should take care of which data you divulge?
Yes, exactly. Publicly-available data does have, perhaps, an advantage. In the past, nothing was written about a person, no-one was photographed or filmed anywhere. Nowadays, the camera is a constant companion. Photos are taken, blogs written and tweets published. When you know that you are transparent and that everyone can see what you do, this perhaps has the effect that you should behave better.
Is there really something to people with nothing to hide - the “transparent man”?
I believe so. Anonymity will probably be a luxury commodity one day. It will be luxury that one’s own tracks will not be recorded.
«A healthy measure of security is necessary in order that confidence in digital media remains.»
Anonymity is probably already difficult whenever we carry our smartphones or other mobile devices on us. Does the use of these devices conceal further risks, in particular whenever we use them on business as a company employee?
Devices such as smartphones and tablets can absolutely be operated in a secure manner. A risk exists in that the devices are much smaller and more mobile than a notebook or computer and thus more easily stolen. For this reason, one should be careful about which and how much information is stored on the devices and how they are protected. A further danger exists in that one can log onto unsecure networks with the mobile devices. Whenever you use the WLAN at the airport or in the hotel, the danger exists that this can be controlled by an attacker.
In companies, cloud-based services are also increasingly offered. Is this per se bad from a cyber-security perspective?
The uncertainty with the cloud is that you do not know exactly where the data is and who has access to the systems and infrastructures. This creates the feeling that the cloud is not secure.
Especially for smaller firms, the cloud can mean better IT security as these firms, with their reduced size, do not always have an individual which looks after the security of the server. The outsourcing of certain data to the cloud is, in such cases, a logical decision as there are specialists there which take care only of security.
The most important security aspect with the cloud is how the user logs on. As soon as an attacker can log onto the cloud of the company, he has all data at his disposal. He does not need to penetrate the company physically or by way of a Trojan. What he, however, needs is a user name, password, certificate or the like. Because of cloud services, phishing is therefore becoming interesting again as it has already almost fallen into oblivion.
In most cases, security means that one’s course of action is restricted. If all security measures are implemented, is a normal workflow still possible?
I find an analogy illustrates this issue very vividly: If, when driving, you follow all safety rules, is driving a car then still possible? That can be answered in the affirmative. You can drive even if you follow certain rules, limit your speed and must know the signals.
At work, it is no different. You need to take certain precautionary measures in order to protect yourself against internet attacks. A healthy measure of security, nothing excessive, is necessary in addition in order that confidence in digital media remains.
«Companies will proceed based on the following reflections: I am aware that I am being attacked but how or how quickly do I notice that I was attacked?»
Are there any trends in attacks which have developed in recent years? Where do you see future trend
The individuals behind cyber-attacks, as a rule, want to earn money, however are increasingly giving up the idea of wanting to earn the money directly. In the meantime, they rather offer services to procure and collect information. Information is the gold of the future! Whoever can tap the right information and combine it cleverly, that person gains control. I believe that the trend will be to increasingly lodge Trojans on devices, in households or in firms. These Trojans collect information and pass it on to large computing centres which combine, correlate and process this information and draw conclusions therefrom. An approach of this kind creates an enormous advance in knowledge.
That sounds like the amassing and processing of information which large eCommerce groups also engage in.
Yes, I believe that one is not at all aware of the fact that information is collected everywhere, where log data is compiled and passed on. This again goes in the direction of the transparent man.
Which general digital trends do you see for the future?
I see the development that financial business will be increasingly decentralised. In this respect, the provocative question can be asked whether banks in their present form will still be needed in future.
Do you mean in this respect that in the process of digitalisation, parties like Fintech companies will emerge and compete with banks for their services?
Exactly. On the one hand, I speak about Fintech companies, on the other, about the community attempting to take central control of itself. When payments are made directly from user to user, the control over payment flows is taken away from financial-service providers. In the process of digitalisation, it happens more and more frequently across sectors so that the intermediary is no longer necessary.
Also, the Internet of Things will continue to heavily preoccupy us, both from the perspective of security as well as from the point of view of automation. The question will arise about everything that is automated and then being able to act for itself.
In addition, supervision and monitoring will take on added importance. Companies will proceed based on the following reflections: I am aware that I am being attacked but how or how quickly do I notice that I was attacked? How am I prepared if it occurs? How do I react or how do I retrench in a manner that certain parts of my information base are not lost? That means that I build up a protection from attacks but know that I will need to live with a residual risk. Banks are very advanced in making risk evaluations and impact analyses. Indeed, they do that already in the case of finances and can adapt it for information.
Is there more security in place for customers so that data with banks is in good hands?
Yes, that could be. I do indeed entrust my assets to the bank. And I know that the bank is always at my disposal and that someone pays attention to my information. I can imagine that banks in future can exploit this confidence to safeguard other information than financial data.